Today we are going to focus on how to secure Secure SSH on Linux.
Users can connect to the server remotely to SSH/Shell is the remote connectivity tool in Linux. To restrict the attacks it is vital to secure SSH/Shell .
Upgrading the SSH is one way however the other methods you need to employ are as follow:
Setup Wheel User
This idea behind this process is to disable Root SSH login and allow a new user or an existing user to the Wheel user group so that only that user is allowed to connect SSH.
#Open the SSH config file
vi /etc/ssh/sshd_config
#Set PermitRootLogin to ‘No
PermitRootLogin no
SSH server settings are stored in the /etc/ssh/sshd_config file. To disable root logins, make sure you have the following entry:
and restart the sshd service:
service sshd restart
If you need root access, login as a normal user and use the su command.
This will disable the Root login.
Warning: If your current session is terminated you can’t login as Root user. Now, you have to create a new wheel user simply with,
adduser <wheel_user_name>
Adding a new user is not necessary, if you want an existing user to be the wheel user, you can skip the above step. Now go to WHM and add the user to wheel user group.
WHM >> Security Center >> Manage Wheel Group Users >> Select the user and click ‘Add to Group’.
Now a wheel user is added and you can only login to SSH as that particular user and after logging in, you can swith to Root.
Setup key based password less login
The idea behind this is to disable password authentication and allow SSH access only by Key based authentication. For this you need to general an SSH key in the machine that you want to connect to the server and add the public key to the authorized keys of the server.
#Open SSH config file
vi /etc/ssh/sshd_config
#Edit the PasswordAuthentication parameter to ‘no’
PasswordAuthentication no
This will disable password authentication in the server.
#Generate SSH key in the host machine (system from which you need to connect to the server)
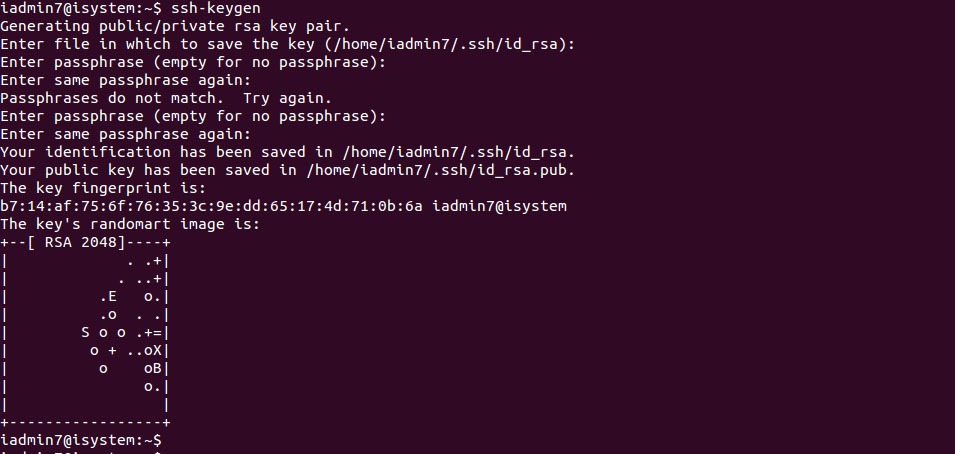
ssh-keygen
This will prompt the file to specify the key which is generated. If you hit ‘Enter’, the key will be placed in ‘/home/user/.ssh/id_rsa’ by default.
It will also ask the desired passphrase, which is similar to password but you’ll only have to add it once. You can refer the screenshot below.
Once the key is generated, you’ll have to add the public key in the authorized keys file in the server. For this you can use scp functionality.
scp -P portnumber ~/.ssh/id_rsa.pub root@XX.YY.XX.ZZ
SSH into the remote server, and in the home directory of the SSH user, you can see the file ‘id_rsa.pub’. Just copy paste the key in the said file to the file ‘/root/.ssh/authorized_keys’
cat id_rsa.pub >> /root/.ssh/authorized_keys
With this, you will be able to login to the server without prompting passwords and only based on the key added,
https://wiki.centos.org/HowTos/Network/SecuringSSH